Weekly Infosec News Brief: 21-27 March 2016
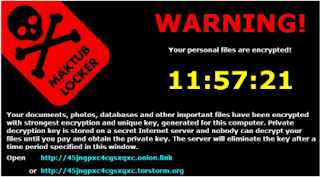
A new strain of ransomware was discovered last week, and is called "Maktub Locker." This ransomware is characterized by its evasive properties once installed; many file locations and even extensions are different on every victim. The ransom demanded to decrypt victims' files is set on a sliding scale so that the ransom increases the longer you wait to pay. This malware is able to function with or without its being able to access any external command & control server, which is unusual and eliminates a common method of limiting the damage from ransomware. Despite all the sophistication, the primary delivery mechanism to date for this scourge has been as a ".scr" file attached to emails, sometimes inside a ".zip" file. Please test your organizational email system to ensure that ".scr" files cannot be received in emails, whether in the form of a zip file or not.
http://www.scmagazine.com/beautiful-ransomware-arrives/article/485432/
http://news.softpedia.com/news/new-maktub-locker-ransomware-comes-with-high-ransom-price-and-beautiful-artwork-502150.shtml
Another bad Java bug (CVE-2016-0636) was revealed recently; in this case it was actually a bug that was found back in 2013 and was just never patched properly. The vulnerability was publicly exposed a couple of weeks ago, and Oracle released a patch just this week. However, researchers were saying even hours after the original patch was released that is was insufficient. This vulnerability can allow a malicious Java applet to access any files on your computer and potentially to take full control of the computer. Please install the patch as soon as possible, or better yet -- get rid of Java on your desktops (or most of them).
http://www.csoonline.com/article/3043203/security/two-year-old-java-flaw-re-emerges-due-to-broken-patch.html
https://blogs.oracle.com/security/entry/security_alert_cve_2016_0636
http://www.securityweek.com/oracle-reissues-patch-two-year-old-java-flaw
NIST is the agency responsible for developing information security standards for the US government, and last week they released new draft documents outlining how agencies should managed the security of remote workers and their connections. Their advice is strong, and would be worth considering for many private organizations as well. While the government has had many infosec issues, their standards are generally quite good -- it's the implementation and compliance that is too often lacking.
http://www.nist.gov/itl/csd/attackers-honing-in-on-teleworkers-how-organizations-can-secure-their-datata.cfm
DOD Temporarily Cut Off Access to Personal Email from Inside Their Network
Over the weekend of the 18th-20th, the Department of Defense cut off access to most popular personal email (webmail) in response to a reported upsurge in phishing and ransomware infections that had been occurring on their systems. This temporary halt highlights two interesting lessons that IT departments should remember. First, that personal email is as much a potential vector for malware as corporate email. Second, it can be helpful to have, and plan for, emergency measures to be taken in the event of incidents to stem the tide of malware infections and the like.
http://www.nextgov.com/cybersecurity/2016/03/pentagon-cut-access-personal-email-fight-malicious-messages/126902/
Microsoft to Introduce a Macro-Blocking Feature in Office 2016
Last week's Infosec New Brief pointed out the continued threat posed by malware based on macros if Microsoft Office. This past week, Microsoft announced that they have added a feature in Office 2016 to allow organizational admins to selectively (or entirely) block the execution of Macros. The functionality is administered via Group Policy. Options include blocking per application and blocking files marked as having been downloaded from the Internet. The function also allows organizations to provide a custom warning to users when macros attempt to run, which they would have to click through to allow the macro to execute.
https://blogs.technet.microsoft.com/mmpc/2016/03/22/new-feature-in-office-2016-can-block-macros-and-help-prevent-infection/
http://www.computerworld.com/article/3047249/security/microsoft-adds-macros-lockdown-feature-in-office-2016-in-response-to-increasing-attacks.html
Last week Apple released iOS 9.3 for the iPhone and iPad and OS X 10.11.4 for the Mac. One key part of the updates is a fix for a cryptographic vulnerability (CVE-2016-1788) in the Messages app in both operating systems that could allow an attacker to intercept text messages or insert their own messages into a conversation. The updates also fix vulnerabilities on both systems' WiFi components, XML parsing libraries, and PDF reading features, all of which could potentially allow for remote code execution (meaning and attacker could exploit these to run their own program code on a victim system). Organizations are advised to upgrade all Apple systems as soon as possible. Apple's statistics show that many iPhone users go several months without installing OS updates -- if you allow non-organizational iPhones to access your data, do you have a means of ensuring their software is kept up-to-date?
http://www.eweek.com/security/apple-updates-os-x-10.11.4-and-ios-9.3-to-boost-security.html
Cisco Releases Semi-Annual Security Advisories for IOS and IOS XE
Last week Cisco published their bundled security advisories for IOS and IOS XE, the operating systems that power the majority of Cisco's key networking products. The advisory includes patches for six vulnerabilities; all but one of these are primarily denial-of-service vulnerabilities; however, denial of service is a very serious issue when it comes to your core routing and switching infrastructure. The other is a confidentiality issue in in Cisco's Unified Communications Manager, which manages Cisco Voice-over-Internet phone systems. These are not necessarily urgent or critical updates, but organizations using Cisco networking gear should check which apply to their equipment and makes plans to upgrade when possible.
https://www.us-cert.gov/ncas/current-activity/2016/03/23/Cisco-Release-Security-Updates
http://www.cisco.com/c/en/us/about/security-center/event-response/cisco-erp-march-2016.html
Verizon Enterprise Breached; Customer Contact Data Taken
A hacker on an internet forum was offering for sale last week a database of information on 1.5M customers of Verizon Enterprise, famed for (among other things) their security breach investigations and annual reports on the same. The full list was offered for a price of $100k, along with information on weaknesses in the Verizon website. Verizon confirmed in a statement that they had found and fixed a vulnerability in their website that had allowed an unknown party to steal contact info on customers. Verizon says the info taken is only basic contact information and nothing more, and that they are contacting affected customers. The incident highlights the difficulty of properly securing web applications. Does your organization have web-based applications that contain sensitive data? Have you had a security assessment done to ensure that data is safe? Contact Anchor to see how we can help!
https://krebsonsecurity.com/2016/03/crooks-steal-sell-verizon-enterprise-customer-data/
http://www.scmagazine.com/data-breach-authority-verizon-enterprise-breached-15-million-customers-impacted/article/485436/





Comments
Post a Comment